 This week, some practical information, as opposed to my lofty, philosophical flights into the realms of high lit’rit’cher. (Which means I’m too tired to think, and am thus beginning to just dump the contents of my brain all over the place. I think it may be a sign of premature senility…)
This week, some practical information, as opposed to my lofty, philosophical flights into the realms of high lit’rit’cher. (Which means I’m too tired to think, and am thus beginning to just dump the contents of my brain all over the place. I think it may be a sign of premature senility…)
Malware. If you own or use a Windows computer, you’re going to get it. Malware is any program which installed on your computer without your knowledge and is intended to either collect information about you or simply to interfere with the efficient running of your computer. I help a lot of friends, family members and co-workers figure out problems with their Windows PCs. 99% of them are caused by malware. As soon as I here these phrases:
“My computer is suddenly really slow!”
“All of my files are gone!”
“When I go on the Internet, a couple of dozen windows open.”
“My home page isn’t what it used to be and I can’t change it back.”
“A window opened and said my computer is infected.”
“None of my programs will run.”
I know we’re probably dealing with malware.
Most malware is written to target Windows computers, because they’re so prevalent in business and in the homes of people who didn’t want to spend a lot on their computer. That’s not to say that people who do want to spend a lot on their computers don’t also buy Windows, but higher-end users aren’t as likely to become victims of malware. They know what it looks like, and they know how to get rid of it.
Malware is designed to take advantage of people who aren’t particularly computer-savvy, people who spent $300 at the Wal-Mart on the latest deal, because they needed a computer to let them get on the Internet and maybe do some homework. These people don’t really want to learn a lot about how computers work, they just want them to work. (Don’t be insulted if that describes you. There’s nothing wrong with just wanting a lightweight computer, and you have the right to expect that, for $300, you’ll get something that works. I wish it were that easy.)
The Biggest reason malware works is that you don’t know what your computer is supposed to do. Seriously. Any Windows user can suffer a malware attack. All of the symptoms above have occurred on PCs I’ve used. It doesn’t mean you were surfing porn (I plead the Fifth) and it doesn’t mean you opened an infected email. A lot of malware is actually embedded in advertisements on sites that are otherwise legitimate. One of the worst malware attacks I ever suffered happened when I opened yahoo.com one day. (That does not mean you shouldn’t visit yahoo.com. It means any site can be a host for malware.)
But getting hit by malware doesn’t mean that the malware has done what it set out to do. It hasn’t actually worked. If the user sees the malware manifest itself and corrects the problem immediately, the malware is defeated. Sadly, a lot of users don’t see the problem for what it is, and so they do exactly what they shouldn’t.
Example:
A window pops up and says, “Your Computer is infected! Do you want me to clean it for you?”
The uneducated user will often answer “yes.” Seems reasonable, right? My computer knew it had malware, and so it told me about the malware, and offered to fix it. I said, “fix it.”
Nine times out of ten, though, the program that is telling you you have malware is, itself, malware. These programs pretend to be legitimate anti-malware or anti-virus programs. They claim to have names like “Anti-Virus 2014” or “Essential Windows Security.” But they’re malware. The only way to know that they’re not part of your computer’s normal behavior is to know what’s on your computer to begin with.
Do you have anti-virus or anti-malware software? If your answer is, “I think so,” you’re in danger. If your answer is “I don’t know,” you’re in danger. If your answer is, “Yes, but I don’t know the name of it…” you get the idea. If you don’t know the names of your security programs and how they behave, you can easily be fooled when a fake security program offers to “fix” something for you.
So learn the name of your anti-virus and anti-malware programs, and, if you don’t have one, get one. There are some decent free anti-virus programs for Windows:
If you do have a window pop up and say “Your Computer is Infected,” assume you have malware and act accordingly. (See below.)
NEVER click YES when a program offers to FIX your Malware, unless you RAN that program. Why not? Because, if the program offering to “fix” your computer is malware, answering yes could tell it to:
– Hide, encrypt or delete data on your drive
– Install more malware
– Transmit information about your computer use (including your usernames, passwords, account numbers, etc) to listeners on the Internet
So what should you do?
Act Accordingly.
There’s a simple little program called Rkill. It needs to be on every Windows desktop. Rkill turns off known malware programs. It stops them from running so they can be removed. See, malware developers are clever. They write their programs knowing that people have security software, and so one of the first things any well-written malware program does is… turn off security software, or block it from running, or stop it from updating. Rkill tries to shut down the malware so it can’t interfere in its own demise. Rkill usually succeeds at this. Of course, malware programs get more sophisticated as they go along, but I’ve never met one that Rkill couldn’t at least make a dent in. I think the most drastic case was a malware program that kept restarting itself, so I had to keep triggering Rkill about every ten seconds so that my anti-malware scan could finish.
So, step 1 in acting accordingly is to run Rkill as soon as you think you’re infected.
Step 2 is to scan for malware. A lot of programs offer to do this for you. I favor a free program called MalwareBytes. There’s a paid version of it, too, which offers to stay installed an actually prevent malware. I’ve been satisfied with the free one.
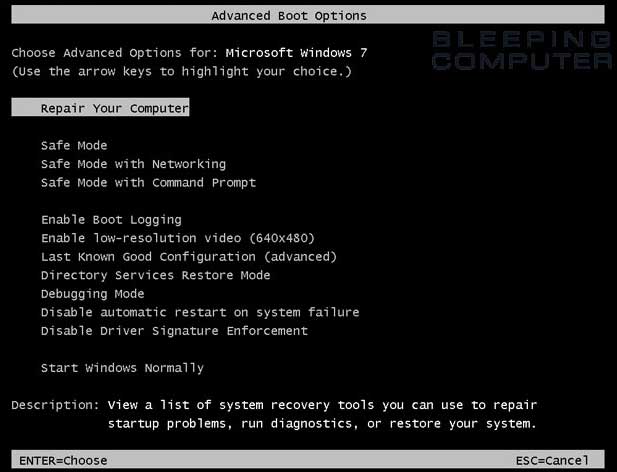 Step 2a is to put your Windows computer in Safe Mode. Safe Mode is a special way of running Windows that doesn’t load a lot of the extra crap the computer doesn’t actually need in order to run. By not loading all this extra crap, you reduce the odds of actually having the malware running, and so you increase the odds of getting rid of the malware. Often people think, after running MalwareBytes or another program, that they’ve eliminated the malware, but they haven’t. It comes back. They way to prevent that is to put the computer in Safe Mode, run Rkill, and THEN run MalwareBytes.
Step 2a is to put your Windows computer in Safe Mode. Safe Mode is a special way of running Windows that doesn’t load a lot of the extra crap the computer doesn’t actually need in order to run. By not loading all this extra crap, you reduce the odds of actually having the malware running, and so you increase the odds of getting rid of the malware. Often people think, after running MalwareBytes or another program, that they’ve eliminated the malware, but they haven’t. It comes back. They way to prevent that is to put the computer in Safe Mode, run Rkill, and THEN run MalwareBytes.
To put a Windows computer in Safe Mode, reboot it, then, before the “Windows” splash screen appears, start pressing the F8 key. Theoretically, you only have to press it once. Me, I just start hitting it repeatedly, as soon as I power the computer on, until I see the black and white screen offering to let me start the computer in Safe Mode.
There are multiple types of Safe Mode offered, including Safe Mode with Command Prompt (you don’t need it most of the time) and Safe Mode with Networking (helpful if your copy of MalwareBytes has not been updated this week. It needs to update every few days, so it knows what the newest types of malware are.) But plain old Safe More works.
You will need to know your Windows username and password to get into Safe Mode. That shocks a lot of people. And it amazes me, as I work on computers, to learn how many people’s passwords begin with “I dunno, try…”
Know your freakin’ password, people. Just know it. It’s 2014 fer Pete’s sake.
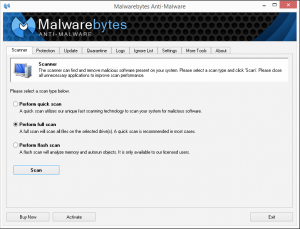 Once you’re in and you run MalwareBytes, first, let it update, then tell it to do a FULL SCAN, and it will search for anywhere from ten minutes to a couple of hours, and find what shouldn’t be there. When it’s done scanning, tell it to get rid of the stuff it found. One last tip — sometimes some of the stuff it found will actually not be selected for removal. Select all that stuff for removal. You want it ALL gone. (You can right-click on any unchecked item and choose “select all” to do this quickly.)
Once you’re in and you run MalwareBytes, first, let it update, then tell it to do a FULL SCAN, and it will search for anywhere from ten minutes to a couple of hours, and find what shouldn’t be there. When it’s done scanning, tell it to get rid of the stuff it found. One last tip — sometimes some of the stuff it found will actually not be selected for removal. Select all that stuff for removal. You want it ALL gone. (You can right-click on any unchecked item and choose “select all” to do this quickly.)
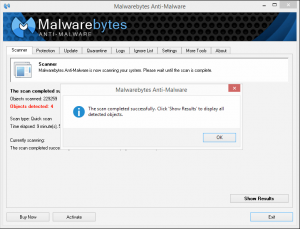
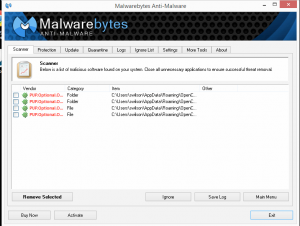
 Once you’ve let MalwareBytes “take out the trash,” restart your computer normally and see how it performs. There may be some residual damage to your setup, especially your home page being reset, and weird toolbars and search engines showing up. I’ll cover those in part two.
Once you’ve let MalwareBytes “take out the trash,” restart your computer normally and see how it performs. There may be some residual damage to your setup, especially your home page being reset, and weird toolbars and search engines showing up. I’ll cover those in part two.
Oh, and one more note about MalwareBytes. When you install it, it will offer you a 30-day free trial of MalwareBytes Pro. Nothing wrong with saying “yes” to that; but… Be aware that, when the 30 days are up, the program will start saying that MalwareBytes Pro has expired and now you need to pay for it. This has confused some people, making them believe that MalwareBytes is no longer free. It’s still free. You just need to remember to deactivate your Pro trial when it expires.
But one last thought for this week:
NEVER EVER EVER buy or install a program which claims to “speed up your computer.” (Or, my favorite, the slogan on dodgy ad sites for MacKeeper: “Please consider cleaning your Mac from junk”) Windows computers slow down for three reasons: Hardware failure, Malware, or Anti-Virus programs which are too aggressive. Less often with modern computers a full hard drive or a badly fragmented hard drive can slow you down too. These “speed up” programs address none of these symptoms. Indeed, they slow computers down. If your computer is slow, check it for malware and then contact support (the computer maker’s or whomever you use) and find out how to run a system diagnostic. A lot of computers have these built in, to tell you if you’ve got bad hardware. Also uninstall any programs you don’t use. But never buy “speed-up” programs.

Great advice, Steve@
I got an anti-virus virus a while back. I now know more about thenWindows registry and various hidden files than Inever wanted to know as Malwarebytes wasn’t able to fix it. If you have another operable computer / mobile device once your computer is in safe mode you can usually figure out how to fix it be doing research on reputable sites.
Yes, sad but true there are cases that MalwareBytes can’t fix, nor can any other removal products. I’m planning to cover those cases a bit. Of course, delving into the registry is beyond many users’ comfort levels. Having another computer (or your tablet or phone) is a good tip. So, in extreme cases, is having a live boot device. I once had to use Linux LiveOS to boot a badly-infected PC and manually perform a system restore.
Steve is right on all accounts! I use all the programs he mentioned and they have saved/protected my computer many times.
Steve–
Great advice and good products. I would ask if I could share this text with some at work–not a copy paste but a referral to the site. I have had my own issues and have used the Rkill (Love that name-makes me feel in control). Thanks–Phil Lord
Sure thing, Phil! I was actually intending to post it for my co-workers too.